
National Security Agency (NSA) whistleblower and Nobel Peace Prize nominee Edward Snowden has once again leaked on how the Agency intercepts “millions” of computers through a so called “implant”.
Described by Snowden’s documents as Turbine, the operation penetrates a unit through a number of ways, including fake Facebook pages, spam emails, unsecured links and “man in the middle attacks” that feeds faux data on a specific computer where the NSA exploits when it sensed that the user is in some web site that it can manipulate.
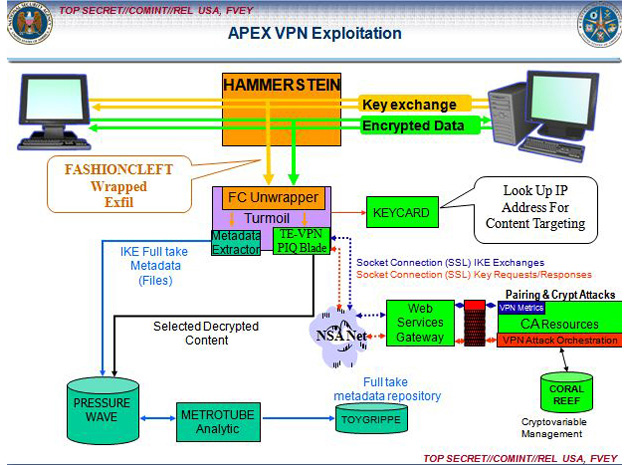
Snowden’s new document also depicted several “implant plug-ins” used by the NSA: CAPTIVATEDAUDIENCE taps a user’s microphone and records their conversations; GUMFISH hijacks web cameras and in turn can capture images and photographs; FOGGYBOTTOM can record and retrieve Internet browsing history and login details, including passwords; GROK deciphers keystrokes users make and SALVAGERABBIT attacks data found in flash drives.
He added that NSA’s main targets are large scale: instead of focusing on a single target, the surveillance agency rather taps into administrators and thereby infecting those that are under their umbrella.
What Snowden unveiled is not entirely new as this was already known that the NSA goes to great length just to get what they want. From using spy techniques that would make Ethan Hunt be just an ordinary layman to infiltrating households with their own creative way, espionage is just a walk in the park for them.
 iTechBahrain Information Technology Digital Marketing Web & Mobile Development Services
iTechBahrain Information Technology Digital Marketing Web & Mobile Development Services