SIEM and SOC are two of the biggest and most important acronyms in cybersecurity. Understanding the SOC vs SIEM relationship – how Security Information and Event Management solutions fit into the Security Operations Center is essential to overcoming some of the most common security challenges.
What is a SOC (Security Operations Center)?
A security operations center (SOC) is responsible for protecting an organization against cyber threats. SOC analysts perform round-the-clock monitoring of an organization’s network and investigate any potential security incidents. If a cyberattack is detected, the SOC analysts are responsible for taking any steps necessary to remediate it.
SIEM: An Invaluable Tool for a SOC Team
SOC analysts need a variety of tools to perform their role effectively. They need to have deep visibility into all of the systems under their protection and to be able to detect, prevent, and remediate a wide range of potential threats.
The complexity of the networks and security architectures that SOC analysts work with can be overwhelming. SOCs commonly receive tens or hundreds of thousands of security alerts in a single day. This is far more than most security teams are capable of effectively managing.
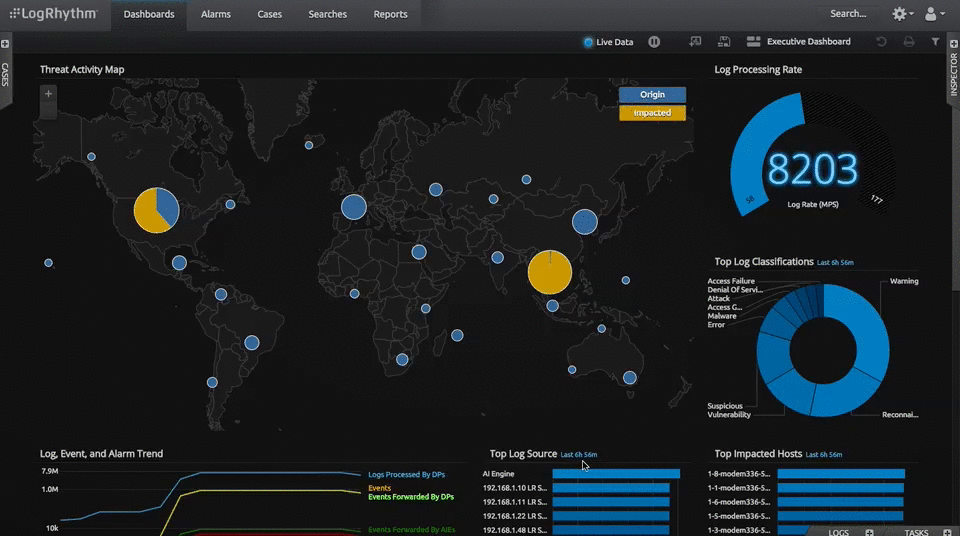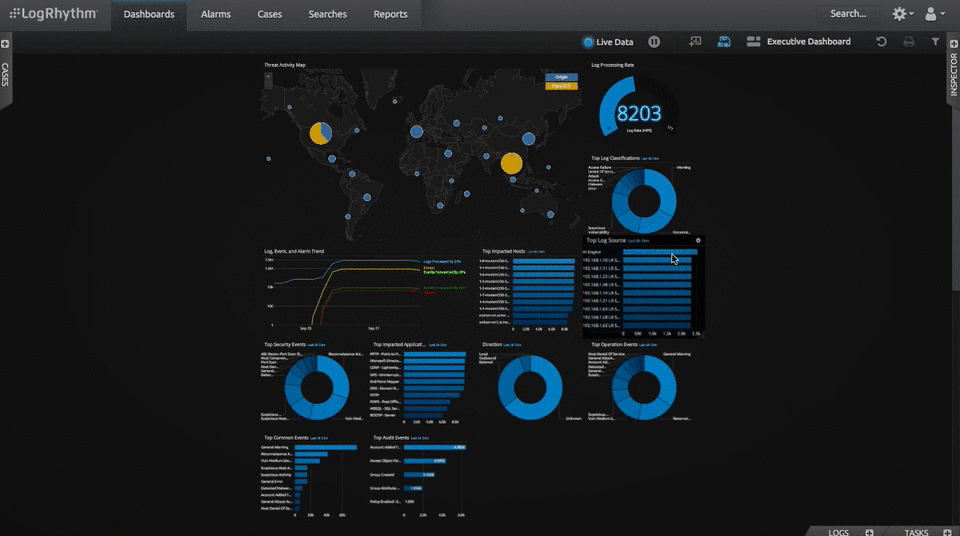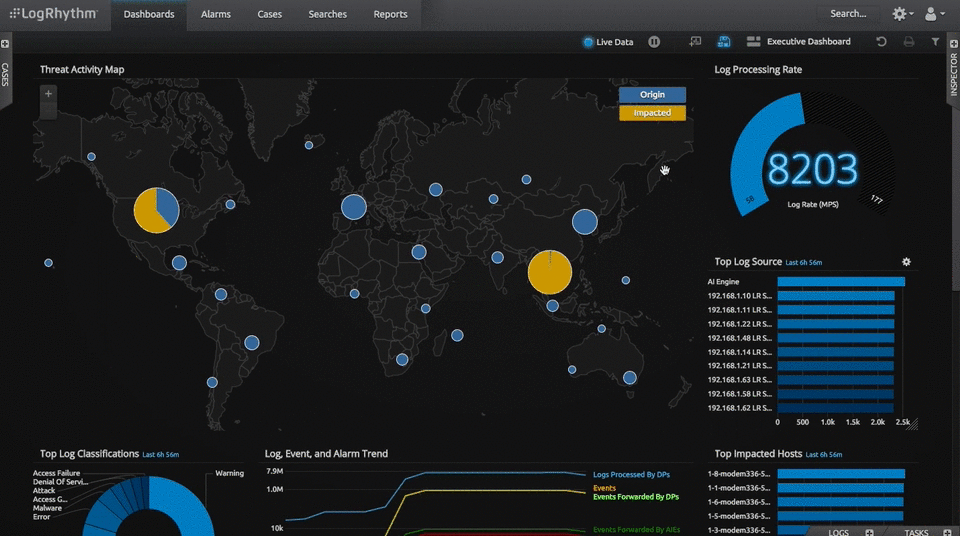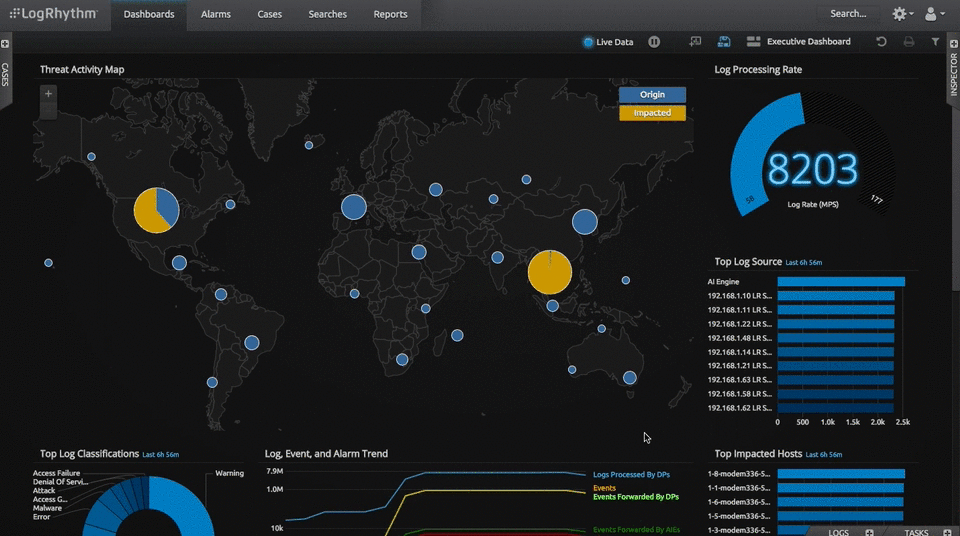
A security information and event management (SIEM) solution is intended to take some of the burden off of SOC analysts. SIEM solutions aggregate data from multiple sources and use data analytics to identify the most probable threats. This enables SOC analysts to focus their efforts on the events most likely to constitute a real attack against their systems.
Advantages of SIEM Systems
A SIEM can be an invaluable tool for a SOC team. Some of the primary benefits of SIEM solutions include:
- Log Aggregation: A SIEM solution will integrate with a wide variety of different endpoints and security solutions. It can automatically collect the log files and alert data that they generate, translate the data into a single format, and make the resulting datasets available to SOC analysts for incident detection and response and threat hunting activities.
- Increased Context: In isolation, most indications of a cyberattack can be easily dismissed as noise or benign abnormalities. Only by correlating multiple data points does a threat become detectable and identifiable. SIEMs’ data collection and analytics help to provide the context required to identify more subtle and sophisticated attacks against an organization’s network.
- Reduced Alert Volume: Many organizations use an array of security solutions, which creates a deluge of log and alert data. SIEM solutions can help to organize and correlate this data and identify the alerts most likely to be related to true threats. This enables SOC analysts to focus their efforts on a smaller, more curated set of alerts, which reduces the time wasted on false positive detections.
- Automated Threat Detection: Many SIEM solutions have built-in rules to help with the detection of suspicious activity. For example, a large number of failed login attempts to a user account may indicate a password guessing attack. These integrated detection rules can expedite threat detection and enable the use of automated responses to certain types of attacks.
SIEM Limitations
Despite their many benefits, SIEMs are not perfect solutions to the challenges faced by SOC analysts. Some of the main limitations of SIEMs include:
- Configuration and Integration: A SIEM solution is designed to connect to a variety of endpoints and security solutions within an organization’s network. Before the SIEM can provide value to the organization, these connections need to be set up. This means that SOC analysts will likely spend a significant amount of time configuring and integrating a SIEM solution with their existing security architecture, which takes away from detecting and responding to active threats to the network.
- Rules-Based Detection: SIEM solutions are capable of automatically detecting some types of attacks based on the data that they ingest. However, these threat detection capabilities are largely rule-based. This means that, while a SIEM may be very good at identifying certain types of threats, it is likely to overlook attacks that are novel or do not match an established pattern.
- No Alert Validation: SIEM solutions collect data from an array of solutions across an organization’s network and use this data for threat detection. Based on the collected data and data analysis, SIEMs can generate alerts regarding potential threats. However, no validation of these alerts is performed, meaning that the SIEM’s alerts – while potentially higher-quality and more context-based than the data and alerts that it ingests – can still contain false positive detections.
 iTechBahrain Information Technology Digital Marketing Web & Mobile Development Services
iTechBahrain Information Technology Digital Marketing Web & Mobile Development Services